

Wednesday, March 26, 2025
Kim Jamerson
You need only scan news headlines to see why software‑as‑a‑service (SaaS) security is so important:
In fact, recent research by Obsidian Security estimates SaaS breaches surged 300% year over year in 2024, with attackers breaching core systems in as little as 9 minutes.
While high‑profile breaches like these get a lot of attention, cyber hacks aren’t the only security risk. Threats can be internal (e.g., your employees) or external (e.g., your SaaS provider’s employees). They can be intentional or stem from human error.
This article explores some of the key challenges to SaaS security and what you should look for in a SaaS provider.

SaaS security encompasses the people, processes, practices, technology, and tools needed to safeguard data stored and accessed via SaaS applications.
Unlike security for traditional software, which is primarily users’ responsibility because the application is stored on local networks or devices, SaaS apps reside in the cloud, and security relies on a shared responsibility model between you and your vendor. SaaS providers manage application security and the underlying infrastructure. Users are responsible for managing data access and security configurations.

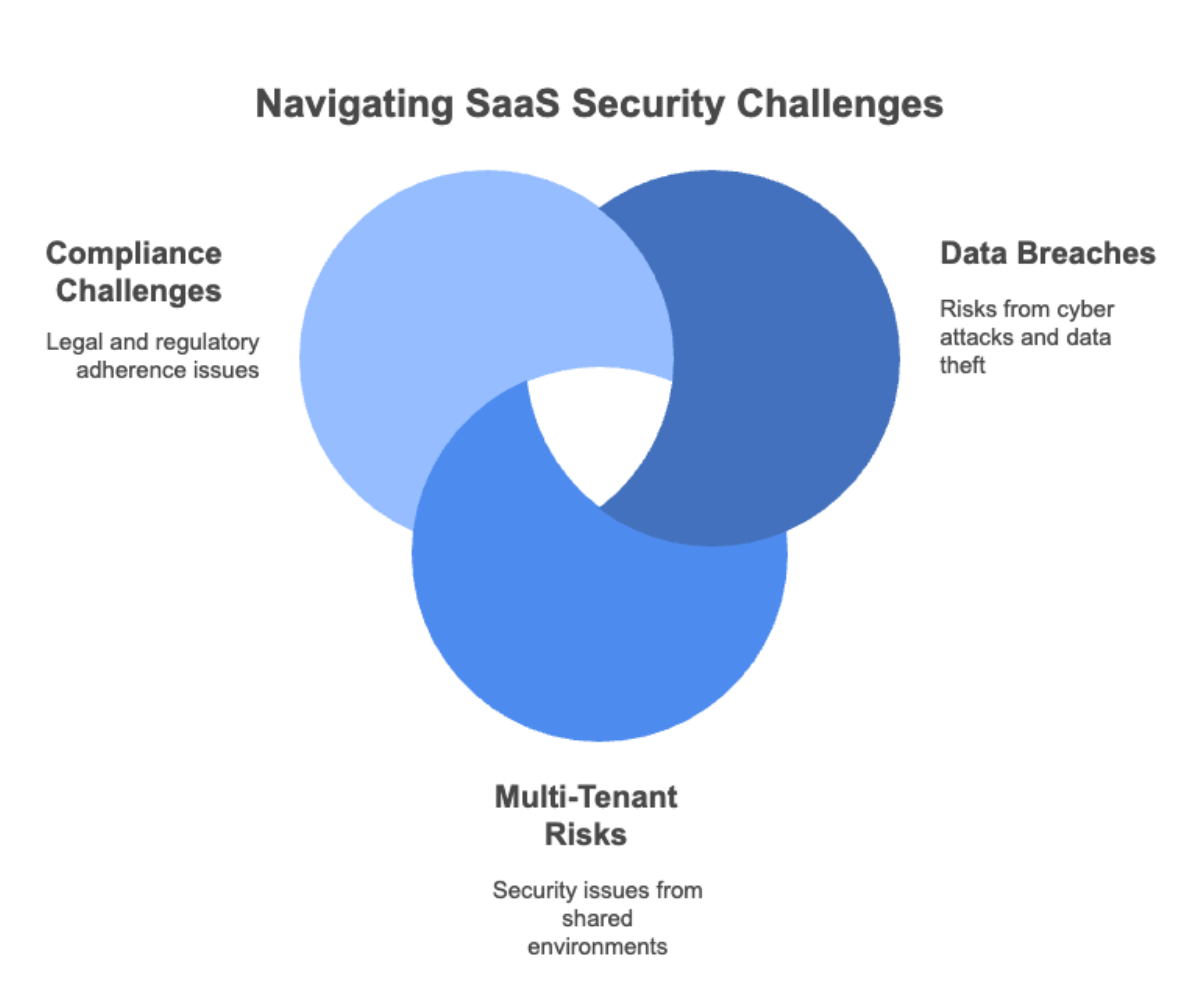
SaaS solutions present numerous unique security challenges that aren’t present or are less prevalent in traditional, on‑premise software.
According to Skyhigh Security, organizations on average currently store 61% of their sensitive data in the cloud, and 90% of them have had one or more cybersecurity breaches, with 80% experiencing data theft specifically. Data breaches put companies at risk of regulatory fines, disruption in business, and damage to their reputations.
Because SaaS solutions are accessible online, they are at a higher risk for cyber attacks.
First, they present a wider attack surface compared to on‑premise software, with more potential entry points for hackers to exploit through APIs, subdomains, and network connections.
Second, improper settings or a lack of knowledge about security best practices can lead to vulnerabilities such as exposed sensitive data or overly permissive access controls. A recent Cloud Security Alliance survey found that 43% of organizations could tie at least one security issue to a SaaS misconfiguration.
Third, SaaS applications often rely on multiple third‑party services, which can introduce additional security risks if those vendors have poor security practices.
With multi‑tenant SaaS solutions, a single instance of the software, database, and hardware serve multiple “tenants” (users or customers). This shared environment can lower the cost you pay for the software, but it can also raise security issues, such as:
There’s a complex web of legal requirements that dictate when, where, and how data is stored, shared, and disposed of—requirements that vary by industry, data type, and region. SaaS platforms can offer features and functionality to address many legal and regulatory requirements, but you’re ultimately responsible for ensuring employees comply with company policies, laws, and regulatory standards.
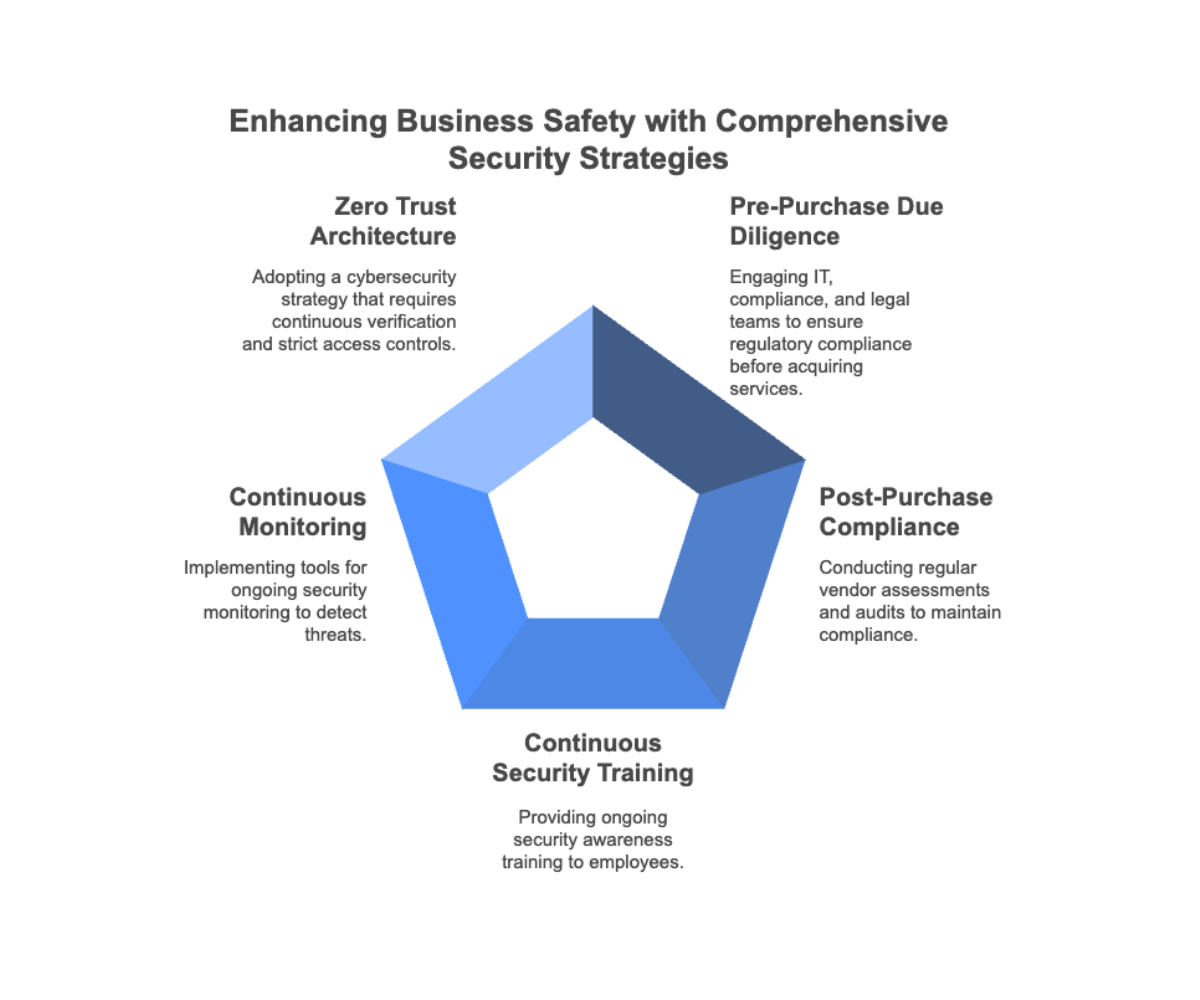
Lean on your legal, compliance, and IT teams for guidance in evaluating SaaS vendors, especially if you’re in a highly regulated industry like healthcare or financial services.
Additionally, look for providers that have proactively complied with industry standards, such as SOC 2 or ISO 27001, which outline security frameworks and procedures for managing, storing, and protecting sensitive data.

When it comes to securing SaaS applications, most companies take a layered approach. They look for SaaS solutions that have built‑in security functionality and use additional technologies to manage security for their portfolio of cloud‑based assets. Three major categories of security tools and functionalities include encryption and secure data storage, identity and access management (IAM), and continuous security monitoring.
Two critical components of SaaS security are data encryption and secure data storage. It’s essential to clearly understand your vendors’ approaches and the tools they provide to manage your security responsibilities.
Data encryption transforms sensitive data into an unreadable format using a cryptographic algorithm to protect the information from unauthorized access. It’s important to ask and understand how data is encrypted “in transit” (data transfers between you and your provider) and “at rest” (data stored on a device or in the cloud). Virtual private networks (VPNs), Transport Layer Security/Secure Sockets Layer (TSL/SSL), and HTTPs are standard tools and protocols to ensure your data is encrypted.
Providers and users share responsibilities for data storage security, which encompasses everything from the physical security of data centers and infrastructure to having redundancies and backups in place in case of a breach or failure, as well as virtual security measures such as firewalls, intrusion detection systems, and other security controls to protect the platform and user devices from external threats.
Be sure to ask providers about:
One of the easiest ways to talk about IAM is to focus on the three A’s of security: authentication, authorization, and accounting.
| Category | Importance | Examples |
|---|---|---|
| Authentication
Verifies users’ identity and confirms they are who they say they are. |
Authentication is one of your first defenses to keep unauthorized people or processes (e.g., executing an SQL query or API call) from accessing your applications and data. | Username & Password, Social Logins (e.g., Google, Facebook, LinkedIn), Single Sign‑On (SSO), Multi‑Factor Authentication (MFA), Biometrics, Magic Links |
| Authorization
Ensures authenticated users have permission to perform actions or access resources/datasets. |
Authorization dictates what users can see and do in an application, including accessing sensitive data like medical records or financial information. Regulatory requirements often come into play here. | Role‑Based Access Control (RBAC), Attribute‑Based Access Control (ABAC), Fine‑grained Access Control |
| Accounting
Tracks and logs user activity within a SaaS application. |
Provides valuable insights into user activity, which can identify misuse and uncover other threats. Regulatory requirements often come into play here. | Audit Logs, Access Monitoring, Compliance Reporting, Billing and Usage Tracking |

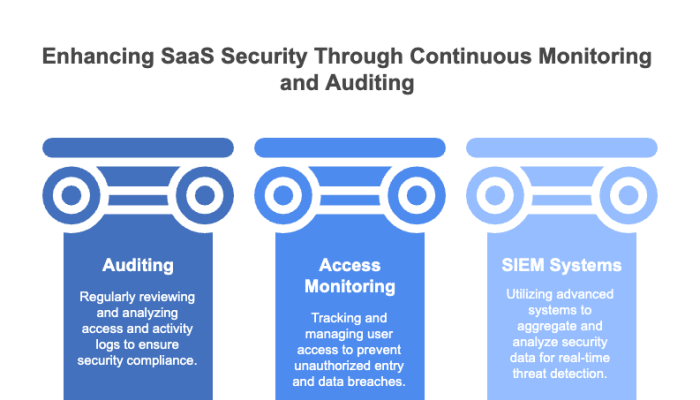
We referenced auditing and access monitoring as part of “accounting” security protocols that may be included within SaaS applications. Continuous security monitoring applies that philosophy to your and your providers’ broader ecosystem of software, hardware, and networks.
Using tools like Security Information and Event Management (SIEM) systems, companies can continuously analyze security data from various sources across their networks to proactively detect potential threats, vulnerabilities, and suspicious activities in real time. This approach allows IT and security teams to assess their organizations’ security posture, mitigate risks, and rapidly respond to incidents when they arise.

Here are a few additional things to keep in mind as you develop your strategies to keep your business safe:
Additionally, depending on your risk assessment, consider implementing a zero trust architecture (ZTA). This cybersecurity strategy assumes no user or device is inherently trusted and requires continuous verification and strict access controls for every request.

The average organization uses a whopping 112 SaaS applications (BetterCloud), many of which they don’t even know about.
Each of those applications presents at least a handful, if not hundreds or thousands, of exposure points to access your company’s data and potentially derail business operations—scary scenarios for any company.
Take a proactive approach to SaaS security to insulate your company from these risks. Download: SaaS Security Unmasked: Hidden Risks You Might Overlook Today.

SaaS solutions present unique security challenges that aren’t present or are less prevalent in traditional, on‑premise software. Data breaches, compliance and regulatory requirements, and risks associated with the multi‑tenant approach many SaaS providers take are common security challenges.
Three major components of SaaS security include encryption and secure data storage, identity and access management (IAM), and continuous security monitoring. Each area includes features and functionalities to allow SaaS providers and users to secure their networks, devices, and data.
Continuous security monitoring analyzes security data to proactively detect potential threats, vulnerabilities, and suspicious activities in real time, allowing IT teams to prevent breaches and rapidly respond if they arise.