
Thursday, March 6, 2025
Kevin Anderson
The widespread adoption of Software as a Service (SaaS) has brought undeniable benefits—scalability, convenience, and cost‑effectiveness. However, relying on third‑party cloud platforms also opens businesses to significant cybersecurity risks. This is where SaaS security monitoring comes in: the practice of continuously tracking and defending your organization against data breaches, unauthorized access, and compliance pitfalls. From detecting threats in real time to automating incident response, SaaS security monitoring helps protect sensitive information and maintain regulatory compliance across multiple cloud‑hosted applications.
In this guide, you’ll learn why SaaS security monitoring is a crucial element of modern business operations, how it works in practice, and which tools can help you mitigate risk in a continuously evolving threat landscape. You’ll also see how real‑time monitoring can prevent costly incidents, maintain customer trust, and keep you compliant with strict regulations—all while allowing you to leverage the benefits of cloud‑based services.

Defining SaaS Security Monitoring
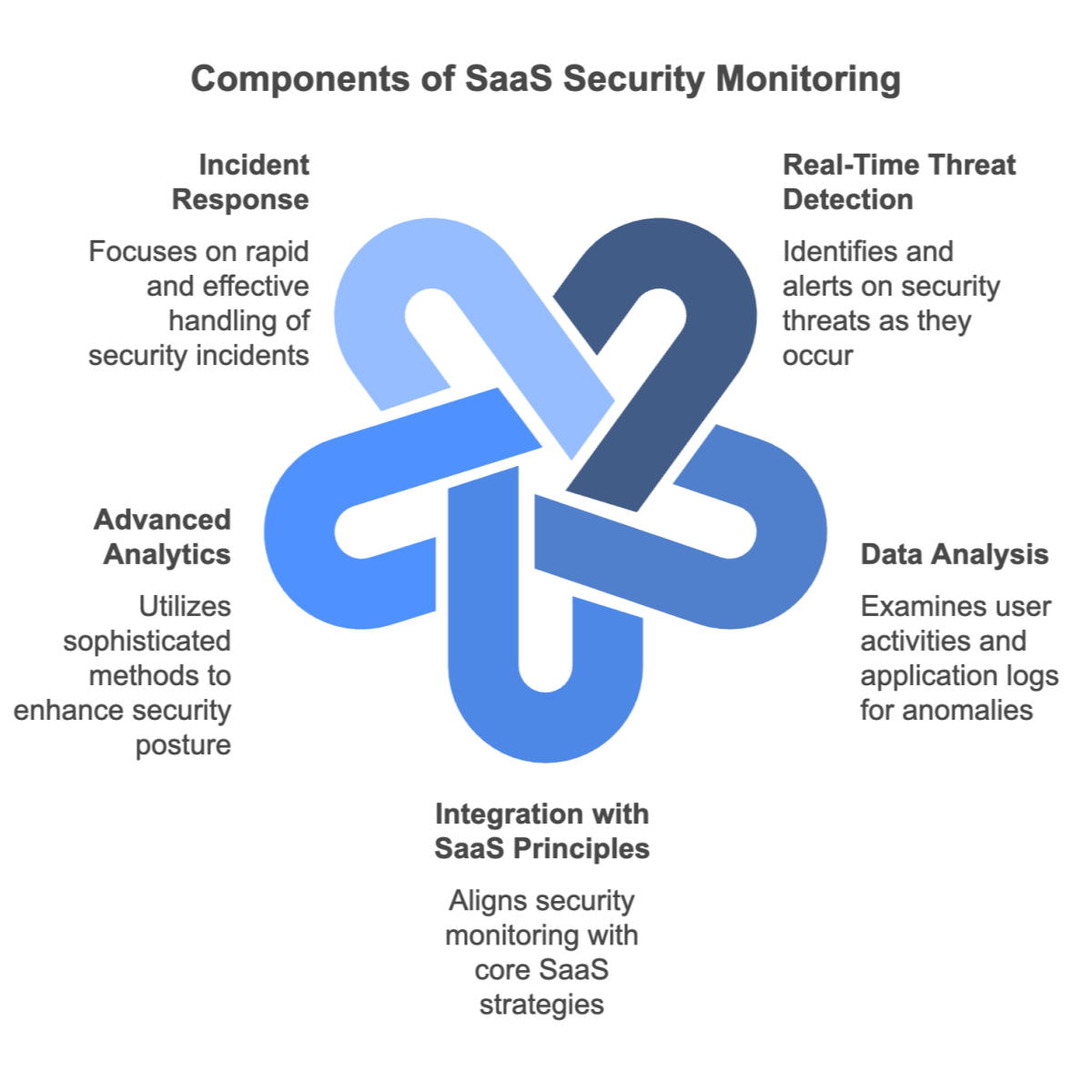
SaaS security monitoring is the systematic process of tracking, analyzing, and responding to security threats and vulnerabilities in your cloud‑hosted software environment. Instead of relying solely on traditional, on‑premises controls, this approach emphasizes continuous, cloud‑based monitoring—examining data from user activities, application logs, and external threat intelligence to detect anomalies as they occur.
Because SaaS applications are hosted off‑site, the visibility and control once enjoyed in a closed network must now extend into external data centers. Real‑time threat detection is critical, providing automated alerts for suspicious behavior such as mass file downloads or unauthorized configuration changes. This capability is especially vital for organizations handling sensitive data—be it financial details, intellectual property, or personal customer information.
To further enhance security, companies are integrating monitoring solutions with foundational SaaS principles and emerging technologies. For example, insights from Digital Transformation and studies on AI Readiness are driving innovative strategies that proactively identify vulnerabilities before they are exploited. Additionally, organizations can benefit from correlating alerts with contextual data, enabling them to prioritize incidents based on severity.
This integrated approach not only minimizes false positives but also empowers security teams to focus on high-priority threats, ensuring rapid and effective incident response. By combining advanced analytics with continuous monitoring, businesses can achieve a dynamic security posture that adapts to evolving risks and supports long-term operational resilience.

The market offers several robust SaaS security monitoring tools designed to provide comprehensive protection. Below are some leading examples along with their key attributes:
Other platforms centralize security management by aggregating logs and threat data from multiple SaaS applications, providing customizable dashboards and detailed reporting features. This variety enables organizations to tailor their security solutions to meet specific operational needs and compliance requirements. For a broader perspective on managing SaaS platforms, explore SaaS Management Platforms.

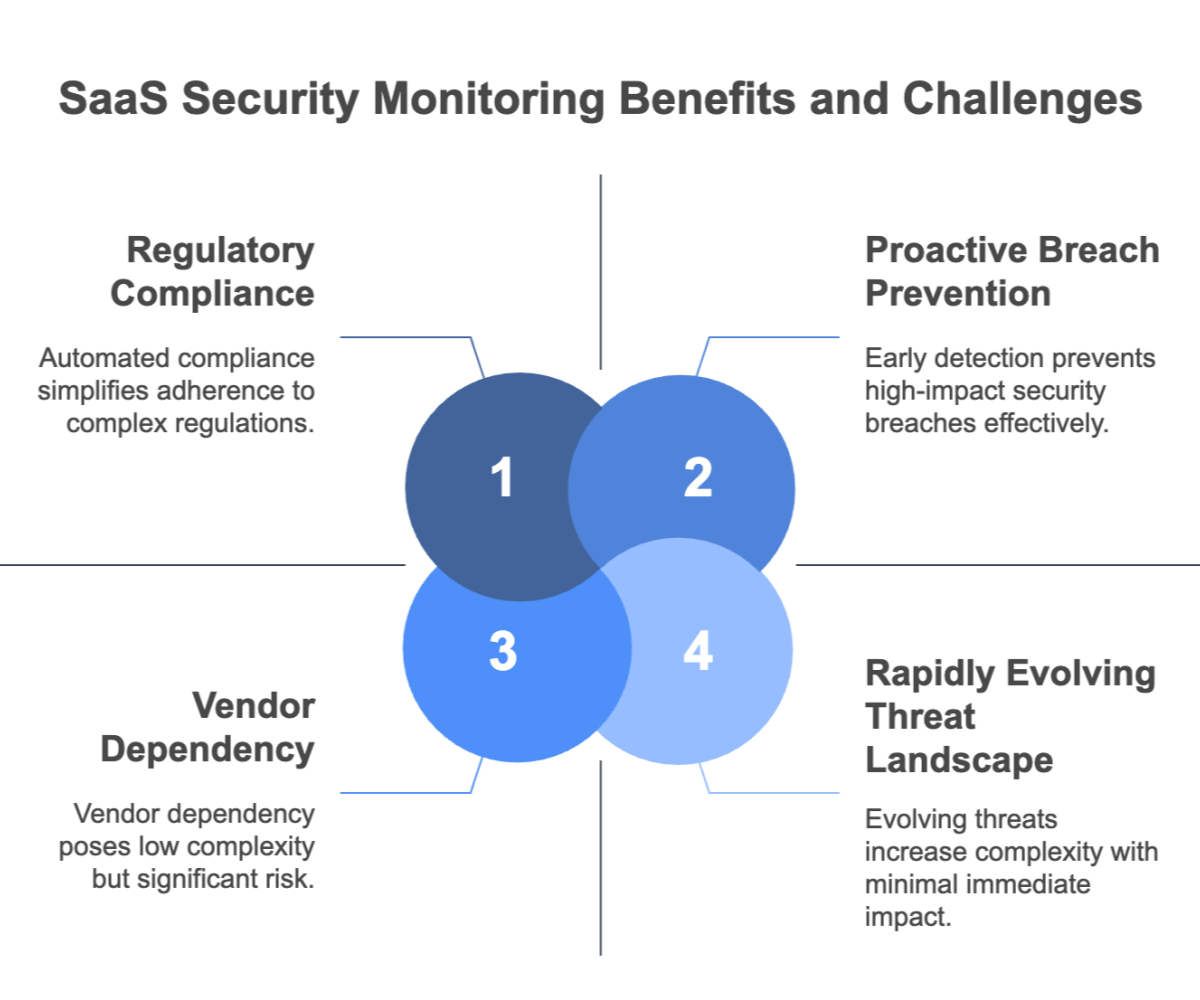
Key Benefits
Common Challenges
To overcome these challenges, organizations must adopt comprehensive strategies that combine innovative technology with regular security audits and continuous employee training. This balanced approach helps ensure that both technological and human factors are aligned to create a secure environment.
Moreover, integrating automated compliance tracking reduces administrative overhead and minimizes the risk of non-compliance. By doing so, companies not only protect their data but also build a resilient security framework that supports long-term business objectives.

Choosing the Right Tools
When evaluating cloud‑based SaaS security solutions, it is important to consider not only the feature set and pricing, but also factors such as:
Recommended Platforms
Other factors to consider include robust real‑time threat detection, advanced user activity monitoring, automated compliance reports, and extensive integration capabilities. For a detailed overview, see Choosing the Right SaaS Security Tools.

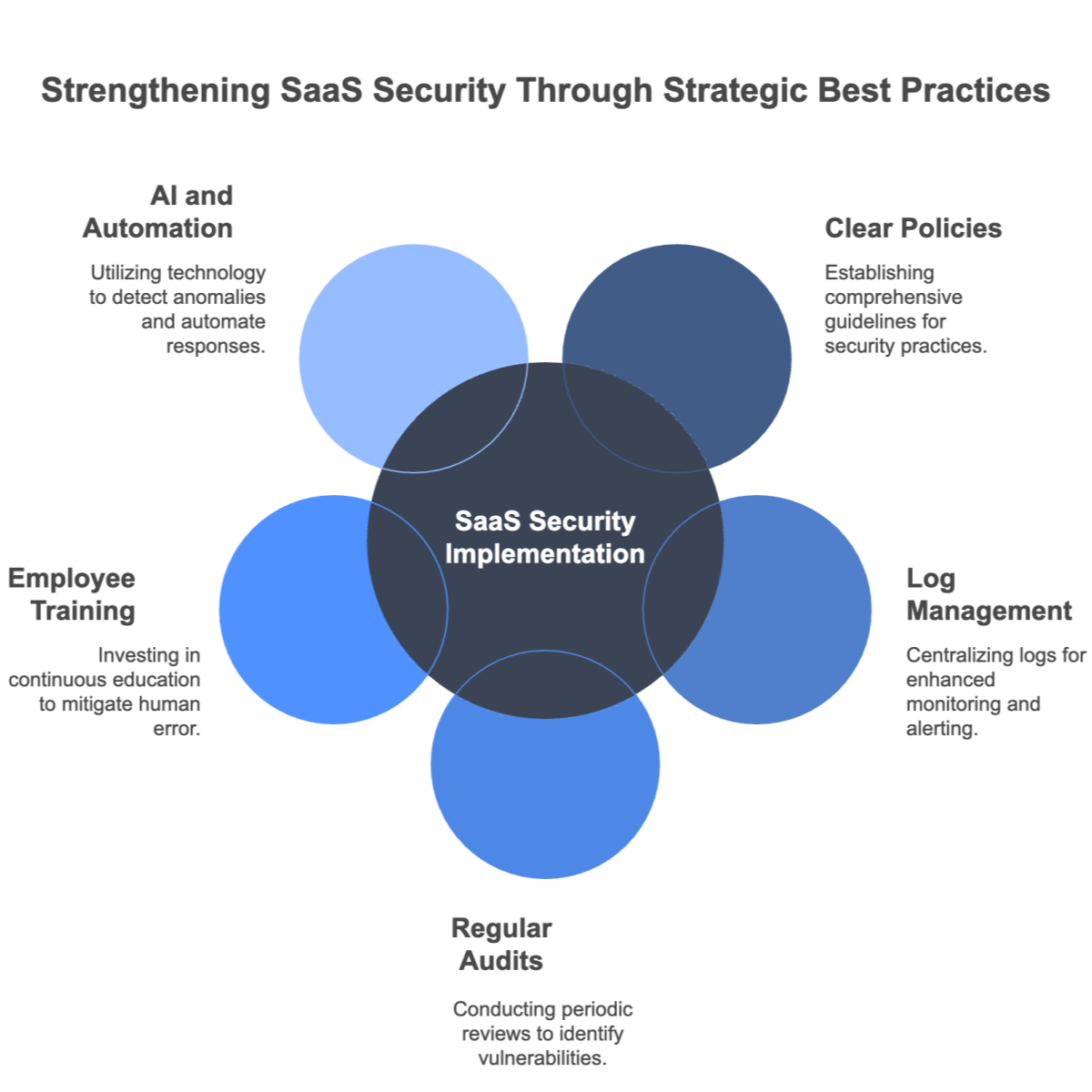
Implementing effective SaaS security monitoring requires a strategic approach that incorporates technology, process, and continuous improvement. Here are some best practices:
Adopting these best practices not only strengthens your security posture but also supports regulatory compliance and operational resilience. For further exploration of industry-specific innovations, consider reading about Vertical SaaS Innovation.

Frequently Asked Questions
What is SaaS security monitoring?
It is the ongoing process of identifying, analyzing, and defending against threats in cloud‑hosted software environments. This typically includes real‑time alerts and automated incident responses.
How do you monitor SaaS security threats?
What are the best tools for SaaS security monitoring?
Leading tools such as Datadog, Vanta, and Microsoft Cloud App Security are popular due to their comprehensive features. The best choice depends on your environment, budget, and compliance needs. For further insights, see SaaS Security Concerns, Risks, Challenges and Solutions.
Why is SaaS security monitoring important?
A proactive security approach helps prevent breaches, protect your brand, and ensure compliance with strict regulations. Without continuous monitoring, vulnerabilities can go unnoticed until they cause significant damage.
How do SaaS providers handle data security?
Most providers use a shared responsibility model—securing the underlying infrastructure while customers manage data governance and access controls.
Can SaaS security be automated?
Yes, automated solutions enable immediate actions such as account lockouts and file quarantines, significantly reducing response times.
How should you choose the best SaaS security solution?
These actionable steps can help you build a robust security framework that minimizes risks and enhances your organization’s overall security posture. For more detailed guidance on security posture, refer to SaaS Security Posture Management: Why It’s Essential.

SaaS security monitoring isn’t just another security add‑on; it’s a strategic imperative in a world where data breaches can shatter customer trust and disrupt entire operations. By investing in SaaS security solutions and integrating them with your existing processes, you safeguard sensitive data, maintain compliance with strict regulations, and ensure business continuity.
Think of security as a proactive partnership between your organization and your SaaS providers. You supply vigilance, comprehensive user education, and robust monitoring tools; the vendor offers secure infrastructure, continuous updates, and specialized security features. Together, you create a formidable defense against evolving cyber threats.
Moreover, organizations that continuously refine their security strategies are better positioned to adapt to emerging risks. Investing in ongoing training, staying current on threat intelligence, and regularly reviewing your security protocols are essential for long-term resilience. For further perspectives on innovative security approaches, explore Smart SaaS Applications.
Download our free eBook “Escape the SaaS Trap” to discover how to build a robust, future‑proof security program and take the first step toward smarter security. You can also explore additional resources such as SaaS Security Unmasked and SaaS Pricing 101 for more insights.