

Wednesday, April 16, 2025
Kevin Anderson
In today’s cloud‑first business world, adopting Software‑as‑a‑Service (SaaS) tools is nearly unavoidable. But while these platforms streamline operations, they also raise an often misunderstood question: who’s really responsible for your data? Welcome to the Shared Responsibility Model—a foundational concept in SaaS that outlines the roles both the provider and customer must play in maintaining security and privacy. Misunderstanding this model is more than a technical gap; it’s a liability waiting to happen.
This blog dives into the gray zones of responsibility in SaaS environments, how to avoid costly assumptions, and why smart companies follow a shared strategy—outlined fully in our eBook Data Privacy in the SaaS Era.

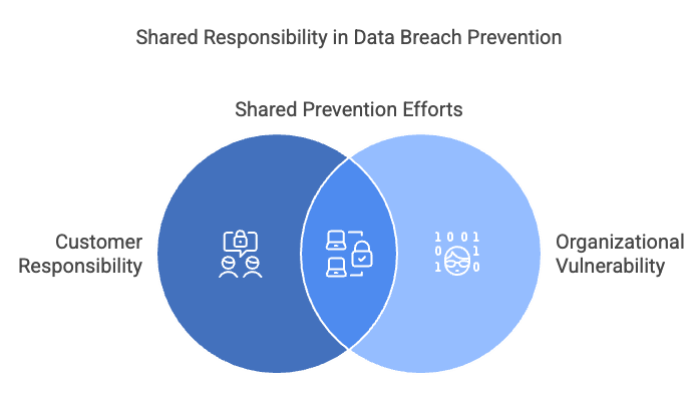
Understanding the Shared Responsibility Model (SRM) starts with recognizing that security in the cloud is a partnership. At its core, the SRM delineates the obligations of SaaS providers versus customers when it comes to protecting data, privacy, and system integrity. It’s not just about uptime and encryption. It’s about governance, access, usage, and control.
SaaS security certifications like SOC 2 and ISO 27001 establish provider baselines, but your team must still configure access, train users, and monitor logs. Aligning with frameworks such as effective SaaS security solutions turns shared theory into day‑to‑day practice.
Provider responsibilities typically include:
Customer responsibilities often involve:
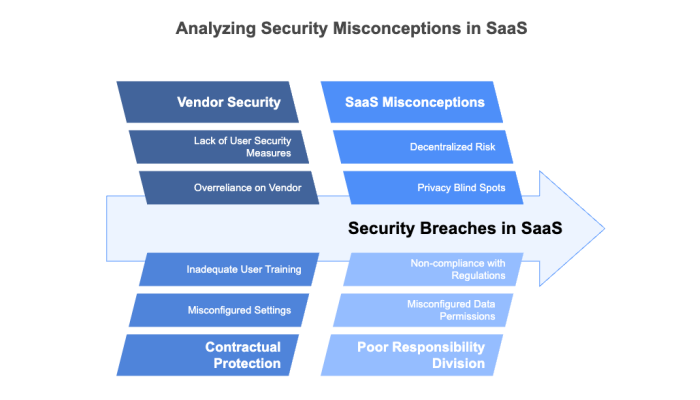
Many businesses assume the vendor “takes care of everything.” That assumption can be costly.


Assumption: “Our vendor is secure, so we’re safe.”
Reality: Vendors secure the platform. You secure the use.
Assumption: “We signed a contract. We’re protected.”
Reality: If you didn’t configure your settings properly, the breach is on you.
Assumption: “It’s SaaS—less to worry about.”
Reality: SaaS decentralizes risk and can introduce privacy blind spots.
According to the eBook, poor division of responsibility often leads to:
Organizations that complete a structured SaaS risk assessment uncover and patch these gaps before hackers do.

As data privacy regulations evolve and enforcement tightens, courts and compliance auditors now look closely at who had the ability to prevent a breach. That’s often the customer. And with many teams using SaaS without direct IT oversight (shadow IT challenges), organizations are more vulnerable than ever.
Gartner estimates that by 2026, 70 % of cloud breaches will involve misconfigurations or inadequate SRM practices. Translating liability into action requires clear ownership of privacy settings, continuous monitoring, and cross‑department coordination—elements too often missing from rapid SaaS rollouts.

| Model | Provider Controls | Customer Controls |
|---|---|---|
| IaaS | Physical hardware, storage, networking | OS, applications, access control |
| PaaS | OS, middleware, runtime, environment | Apps and data configuration |
| SaaS | Entire stack and application | Data input, access settings, usage policies |
With SaaS, you might control less infrastructure, but you're still on the hook for data configuration, privacy governance, and employee behavior.

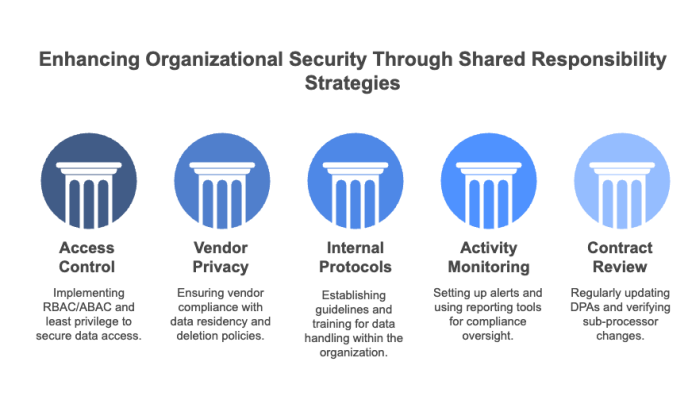
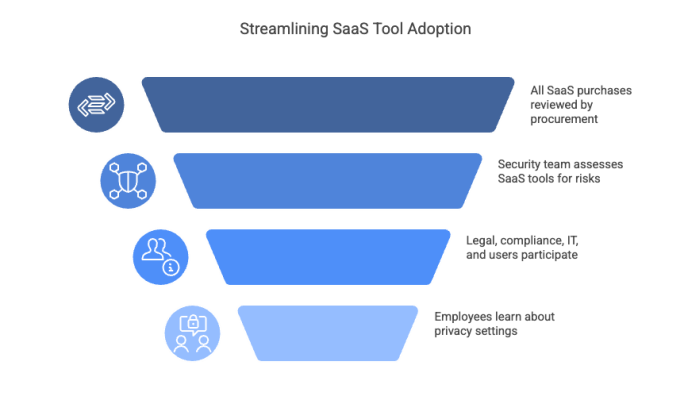
Here’s how your organization can fulfill its shared responsibility role effectively:
For advanced guidance on contract terms and cost containment, see hidden SaaS fees that often slip into renewals.

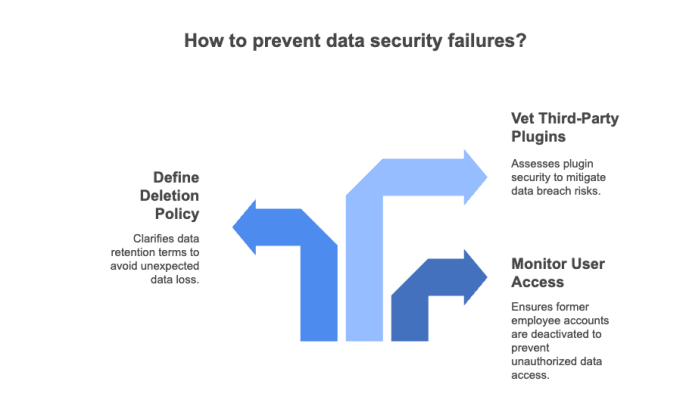
Failure 1: Unmonitored User Access – A marketing team retains access to former employee accounts in a CRM tool. Six months later, that account is used to export sensitive client lists. Who’s responsible? You are.
Failure 2: Undefined Deletion Policy – A company cancels a subscription to a project management tool. Months later, they realize the provider permanently deleted archived project files. But they never clarified retention terms. That’s a shared failure.
Failure 3: Third‑Party Plugins – A third‑party tool integrated with your SaaS platform introduces a data breach. If you didn’t vet the plugin or monitor access, liability may fall partly on your side.
According to SaaS security concern studies, over 60 % of breaches stem from misconfigurations similar to these scenarios.

Most global data regulations acknowledge shared responsibility but place heavy burdens on data controllers—typically the customer in SaaS contexts.
Your SaaS provider can’t cover your legal exposure alone. Mapping SRM duties against frameworks outlined in choosing the right SaaS security tools helps reduce gaps.


Departments often add SaaS tools without informing legal, privacy, or IT. This shadow IT practice undermines SRM by bypassing safeguards.
Action Plan:
Embedding governance early prevents costly cleanup later.

The Data Privacy in the SaaS Era eBook includes a practical Shared Responsibility Checklist, helping you evaluate:
It’s a must‑use tool to reduce guesswork and boost confidence.

In the modern SaaS environment, security isn’t set‑and‑forget. It’s a partnership. Vendors may build the walls, but you decide who gets a key. By understanding and applying the Shared Responsibility Model, your business can confidently manage privacy, minimize risk, and stay compliant—even as SaaS usage expands.
Download the full eBook: Data Privacy in the SaaS Era and get clarity on your SaaS risks and responsibilities—before someone else defines them for you.
