

Friday, March 7, 2025
Kevin Anderson
Software-as-a-Service (SaaS) has become a cornerstone of modern business operations, enabling teams to collaborate, store data, and access sophisticated applications without the need for on‑premises infrastructure.
However, as reliance on cloud‑based solutions grows, so does the potential for data breaches, regulatory violations, and cyber threats. That’s where SaaS security standards and certifications come into play. These frameworks act as guardrails, ensuring that both providers and customers meet essential security and compliance benchmarks. In today’s digital era—where digital transformation is driving change—adhering to these standards is not only a compliance requirement but also a competitive advantage.
By following robust security protocols, organizations can protect sensitive data and build trust with their customers. For more insights on transforming your business digitally, check out our guide on getting started with digital transformation.

SaaS security standards are comprehensive frameworks, guidelines, or regulations that define how SaaS providers must protect sensitive data and ensure operational integrity.
These standards set minimum requirements for practices such as data encryption, two‑factor authentication (2FA), and robust identity management. By adhering to these standards, providers can guarantee that their platforms maintain the confidentiality, integrity, and availability of data, while also enabling customers to meet regulatory compliance.
In today’s interconnected world, these standards are crucial for mitigating cyber threats and ensuring that cloud‑based applications operate safely. For a deeper understanding of cloud security practices, read our article on what is SaaS.

Adhering to SaaS security standards is non‑negotiable for several key reasons. Regulatory compliance is one of the primary drivers; many organizations operate in industries bound by strict laws such as GDPR, HIPAA, or PCI DSS.
Compliance not only prevents legal penalties but also fosters customer trust. Furthermore, clear security standards reduce the risk of data breaches and other cyber threats by ensuring that security controls are consistently implemented across all cloud environments.
This uniformity makes it easier for organizations to evaluate vendors and compare solutions on a like‑for‑like basis. Additionally, having a defined standard provides a roadmap for continuous improvement and helps safeguard against emerging threats. For insights into overcoming security challenges in cloud environments, check out our discussion on SaaS security concerns.

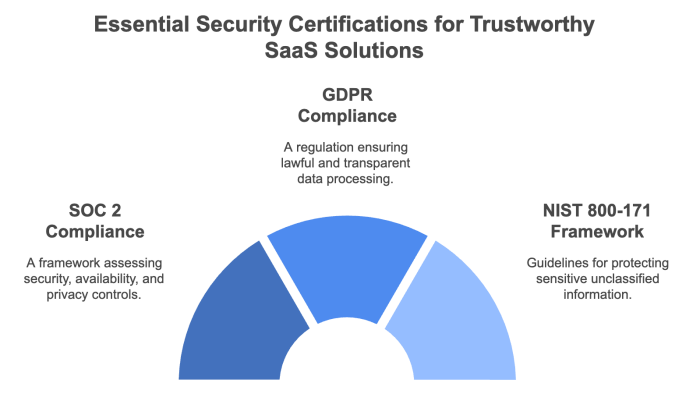
Among the various security certifications available, a few have emerged as industry benchmarks that SaaS providers must aim to achieve. These certifications not only validate the provider's security posture but also serve as a critical factor in vendor selection for security‑conscious customers. Key certifications include SOC 2, GDPR compliance, and the NIST 800‑171 framework.
Each of these certifications focuses on different aspects of data protection and compliance, from enforcing strict access controls to ensuring proper data residency and risk management. They serve as independent validations that a provider is committed to maintaining high security standards. For more detailed strategies on securing your cloud environment, explore our guide on SaaS Security Monitoring.
SOC 2 is a widely recognized framework that assesses a company’s controls related to security, availability, processing integrity, confidentiality, and privacy.
For SaaS providers, achieving SOC 2 compliance demonstrates that they consistently apply rigorous security controls, an essential factor when safeguarding multi‑tenant environments. This certification involves detailed audits by independent third parties who verify that the provider meets all required criteria.
GDPR (General Data Protection Regulation) is a critical framework for any SaaS provider handling data from European Union citizens. It mandates strict data privacy and protection measures, ensuring that customer data is processed lawfully and transparently.
For organizations that need to comply with GDPR, selecting a provider with proven GDPR compliance can significantly reduce the risk of fines and reputational damage. Additionally, GDPR compliance is a strong indicator of a vendor’s commitment to data security.
Developed by the U.S. National Institute of Standards and Technology, the NIST 800-171 framework outlines the security requirements for protecting Controlled Unclassified Information (CUI) in non‑federal systems.
This certification is particularly relevant for SaaS providers that work with government contracts or handle sensitive information that, while not classified, still demands a high level of security. By following NIST guidelines, providers ensure robust controls are in place to mitigate risks associated with data breaches.

Despite originating from various regulatory bodies and industry groups, many SaaS security standards converge on a set of core elements that every provider must address to ensure robust protection of data and systems.
These elements form the foundation of any secure SaaS environment and are critical for both vendors and customers alike. They include comprehensive data encryption, multi‑factor authentication, and stringent credential management.
By implementing these core practices, organizations can build a resilient security posture that not only meets compliance requirements but also deters sophisticated cyber threats. For additional context on safeguarding sensitive data, visit our post on SaaS Data Ownership and Portability.
Data encryption is the process of converting sensitive data into an unreadable format using cryptographic algorithms. This is vital for protecting data both at rest and in transit.
Encryption ensures that even if unauthorized individuals gain access to the data, they will not be able to decipher it without the appropriate decryption key. Common protocols such as TLS 1.2 or higher, AES-256, and VPNs are standard measures that underpin secure SaaS environments.
Implementing Two-Factor Authentication (2FA) is crucial for enhancing security in SaaS applications. By requiring a second form of verification—such as a one-time code or biometric confirmation—2FA significantly reduces the risk of unauthorized access due to compromised passwords.
This additional layer of security is particularly important in cloud environments where user credentials can be targeted by phishing or brute-force attacks.
Effective credential and key management is essential to maintain the integrity of access controls within SaaS platforms. This involves regular rotation of passwords and API keys, secure storage using hardware security modules (HSMs) or vaults, and strict access controls to ensure only authorized users can retrieve or use sensitive credentials.
By adhering to best practices in key management, organizations can reduce the likelihood of data breaches stemming from credential exposure.

Ensuring compliance with SaaS security standards is a continuous process that requires a combination of technology, process, and oversight. Providers must not only implement robust security controls but also demonstrate through regular audits and certifications that these measures are effective.
This is critical for organizations that must adhere to strict regulatory requirements such as GDPR, HIPAA, or SOC 2. Compliance efforts are often supported by advanced tools that automate the monitoring and reporting of security configurations, reducing the manual effort required to maintain a secure posture.
For further details on how these controls integrate with overall digital transformation strategies, read our article on How to Build a Successful SaaS Business Model.

While SaaS security standards offer a clear framework for protecting cloud‑hosted applications, implementing these standards comes with its own set of challenges. Managing multi‑tenant environments, ensuring continuous compliance amidst evolving regulations, and securing integrations with third‑party services can complicate the process.
These challenges require ongoing attention and adaptation, as security threats continue to evolve rapidly. Organizations must invest in employee training, robust monitoring tools, and continuous risk assessments to keep pace with the dynamic threat landscape.
Additionally, aligning security measures across different SaaS platforms can be difficult due to variations in vendor practices and technology stacks. For more information on overcoming these obstacles, explore our insights on SaaS Security Concerns.
In a multi‑tenant SaaS model, multiple organizations share the same infrastructure and applications. This shared environment can make it challenging to enforce strict data separation and security controls for each tenant. A single misconfiguration may potentially expose data across multiple clients, leading to a significant security risk.
Regulatory requirements are continuously evolving. Organizations must not only implement initial security controls but also update and audit these measures regularly to remain compliant. This dynamic environment demands proactive management and periodic reassessment of security policies.
SaaS solutions often integrate with a variety of third‑party services, each introducing its own set of security challenges. Ensuring that these integrations do not become weak links in your security posture requires thorough risk assessments and constant monitoring of all connected applications.

In today’s rapidly evolving digital landscape, adherence to SaaS security standards and certifications is not merely a compliance checkbox—it is a strategic imperative. By implementing robust standards such as data encryption, 2FA, and comprehensive credential management, organizations can protect sensitive information, maintain regulatory compliance, and build trust with customers.
As cyber threats continue to grow in sophistication, the importance of a proactive security framework cannot be overstated. Providers that invest in these standards are better equipped to manage risks, while customers can make more informed decisions when selecting SaaS partners.
Ultimately, a strong security posture ensures that your cloud‑based applications remain resilient, scalable, and secure in the face of evolving challenges. For more perspectives on securing your cloud journey, you might also read our article on Vertical SaaS vs. Horizontal SaaS.
Ready to dive deeper into SaaS security standards and certifications? Download our free eBook, "SaaS Security Unmasked", to explore comprehensive insights on:
Below are some frequently asked questions about SaaS security standards and certifications, along with detailed answers to help guide your security strategy.
SaaS security standards are established frameworks and guidelines—such as SOC 2, GDPR, and NIST 800‑171—that define the minimum security requirements for protecting data in cloud‑hosted environments. They cover aspects like encryption, access control, and incident response to ensure that providers maintain a robust security posture. For further reading on cloud security fundamentals, see our article on digital transformation.
Certifications like SOC 2 and GDPR serve as independent validations that a SaaS provider adheres to rigorous security standards. They help build trust with customers by demonstrating a commitment to data protection and compliance, which is essential in avoiding reputational damage and regulatory fines.
Encryption is critical in safeguarding sensitive data both at rest and in transit. It ensures that even if data is intercepted, it remains unreadable without the proper decryption key. This practice is fundamental for compliance with standards such as SOC 2 and GDPR.
Providers ensure continuous compliance by implementing automated tools that monitor and audit security configurations in real time. Regular internal audits and third‑party assessments further help maintain adherence to regulatory requirements.
Key challenges include managing multi‑tenant environments, adapting to ever‑evolving regulations, and securing third‑party integrations. Addressing these issues requires a proactive approach that combines robust technology, ongoing employee training, and continuous risk assessments.

For additional insights on securing your cloud environment and optimizing SaaS security, explore these related articles: