

Wednesday, March 26, 2025
Kim Jamerson
Conducting a software‑as‑a‑service (SaaS) risk assessment is pretty straightforward when you have one or two SaaS apps. However, once you expand your mix of SaaS solutions, assessing your risk of data breaches and protecting your business from unwanted intrusions can get exponentially more complicated quickly.
Believe it or not, organizations use an average of more than 100 SaaS applications, many of which they have no visibility into—a.k.a. shadow IT—as employees adopt low‑ or no‑cost SaaS solutions without triggering IT, finance, and legal approval.
This mix of the unknown plus the potential risk of exposure—financially, legally, and operationally—has turned into many sleepless nights for leadership teams.
Alleviating those concerns is where SaaS risk assessments come into play. They can help companies identify and mitigate threats tied to SaaS solutions using a combination of technologies, training, and other tools to protect sensitive data and their businesses. For additional insight on emerging trends in SaaS security, check out What is SaaS? to understand the broader ecosystem in which these assessments operate.

A SaaS risk assessment evaluates and identifies potential dangers of data breaches and other harms based on an organization’s use of SaaS applications. These risks may include security vulnerabilities, operational hazards, and risks related to non‑compliance with laws and regulations.
Companies in highly regulated industries have explicit requirements to adhere to, but all businesses face internal and external threats from bad actors or human mistakes. Regular risk assessments of both vendors and internal practices can mitigate your exposure. This process is critical not only for maintaining compliance but also for ensuring that the overall risk profile of your SaaS environment is continuously monitored and updated.
By incorporating automated monitoring and periodic manual audits, organizations can achieve a deeper understanding of their security posture. As detailed in SaaS Security Concerns, Risks, Challenges and Effective Solutions, leveraging multiple assessment techniques is essential for a holistic view of SaaS risk.
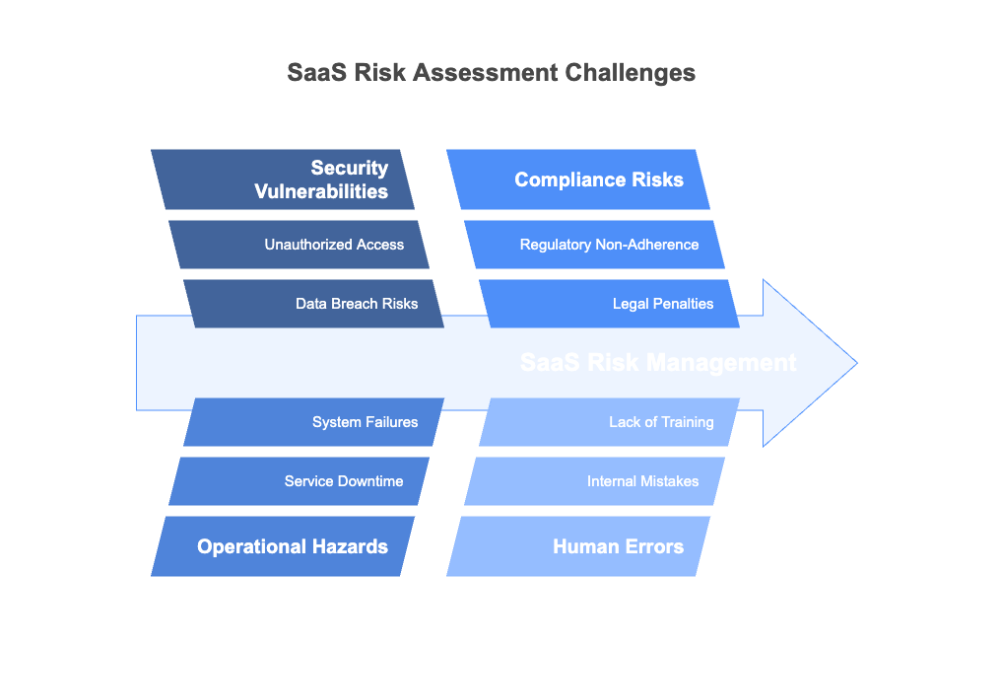

The foundation of a thorough SaaS risk assessment lies in identifying and addressing several critical components. These components ensure that all aspects of potential exposure are systematically examined and mitigated.
Effective risk assessments consider not only technological vulnerabilities but also procedural and human factors. By evaluating the security measures implemented by SaaS providers and the internal practices of an organization, companies can develop a comprehensive view of their risk landscape.
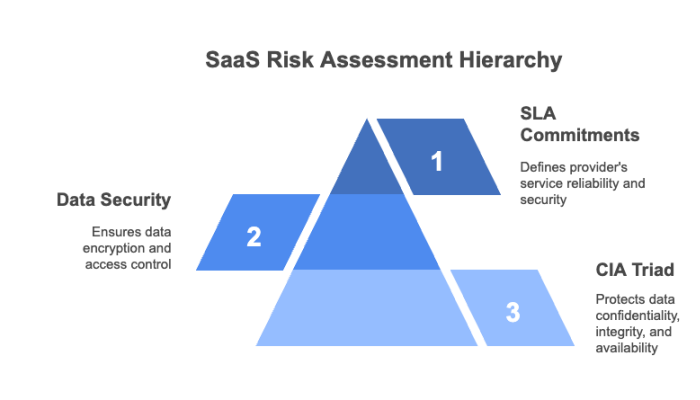
The CIA triad represents the three pillars of information security. It focuses on:
This balanced approach helps protect against unauthorized access while providing the necessary information flow to support business operations. For further details on maintaining a robust security framework, refer to Choosing the Right SaaS Security Tools.
Data security is a critical focus in any SaaS risk assessment. Key measures include:
These measures not only protect against external threats but also help guard against internal errors and misconfigurations. To understand more about the importance of data security, see SaaS Data Ownership and Portability: Don’t Be a Vendor Hostage.
SaaS providers detail their security-related processes and commitments in several legal documents, including Terms & Conditions, End‑User License Agreements, and especially Service Level Agreements (SLAs). SLAs are critical for risk assessments because they specify:
Reviewing these agreements is vital to understand how a provider manages risk and ensures the reliability of their services. For additional insights, you might explore SaaS Security Monitoring.

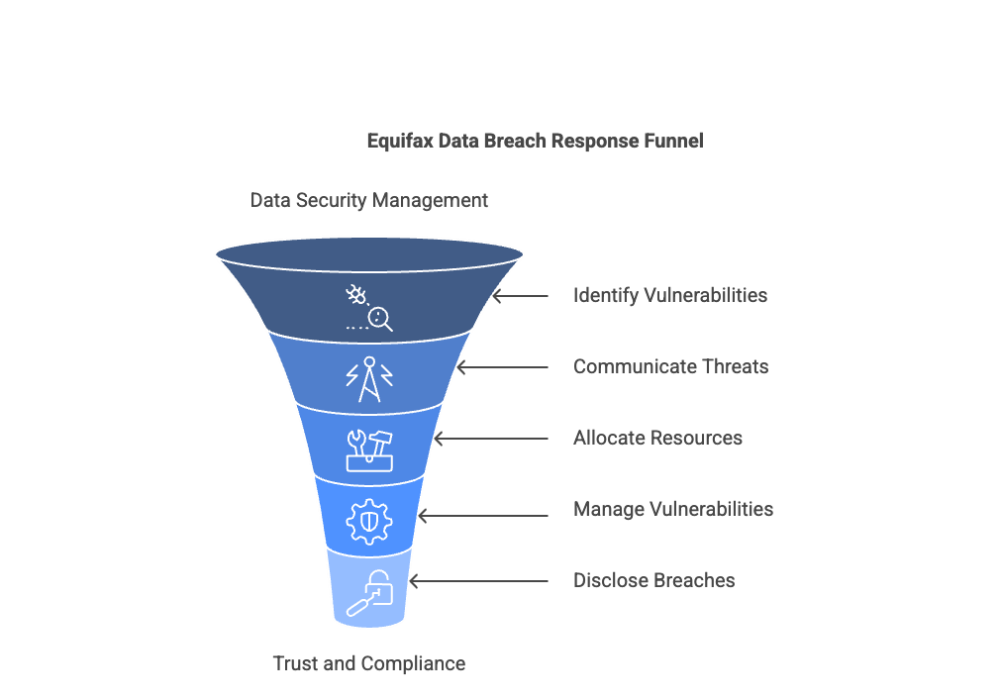
Conducting a detailed risk assessment involves a systematic approach to identifying vulnerabilities and developing strategies for mitigation. This process is crucial for protecting sensitive data and ensuring that potential threats are addressed before they lead to significant breaches.
Key steps include:
This methodical process not only identifies current vulnerabilities but also helps create a roadmap for continuous security improvement across all SaaS applications.


Let’s take a look at one company’s costly data security mistake.
As stated by Federal Trade Commission Chairman Joe Simons, "Companies that profit from personal information have an extra responsibility to protect and secure that data." Similarly, Consumer Financial Protection Bureau Director Kathleen L. Kraninger emphasized that evolving cyber security threats demand rigorous protection of personal information.

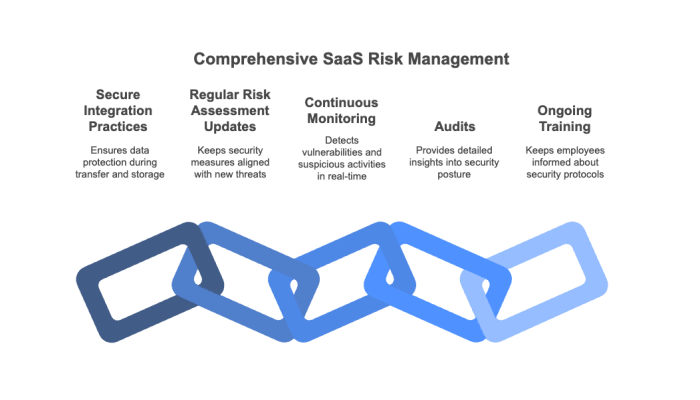
As you review your risk assessments, you will undoubtedly identify issues that can be immediately resolved alongside others that require ongoing attention. To effectively manage SaaS risks, consider the following best practices:
Studies show that IT professionals spend a significant portion of their time on quarterly audits and compliance reviews; by integrating continuous monitoring solutions, companies can significantly reduce this burden while enhancing overall security.

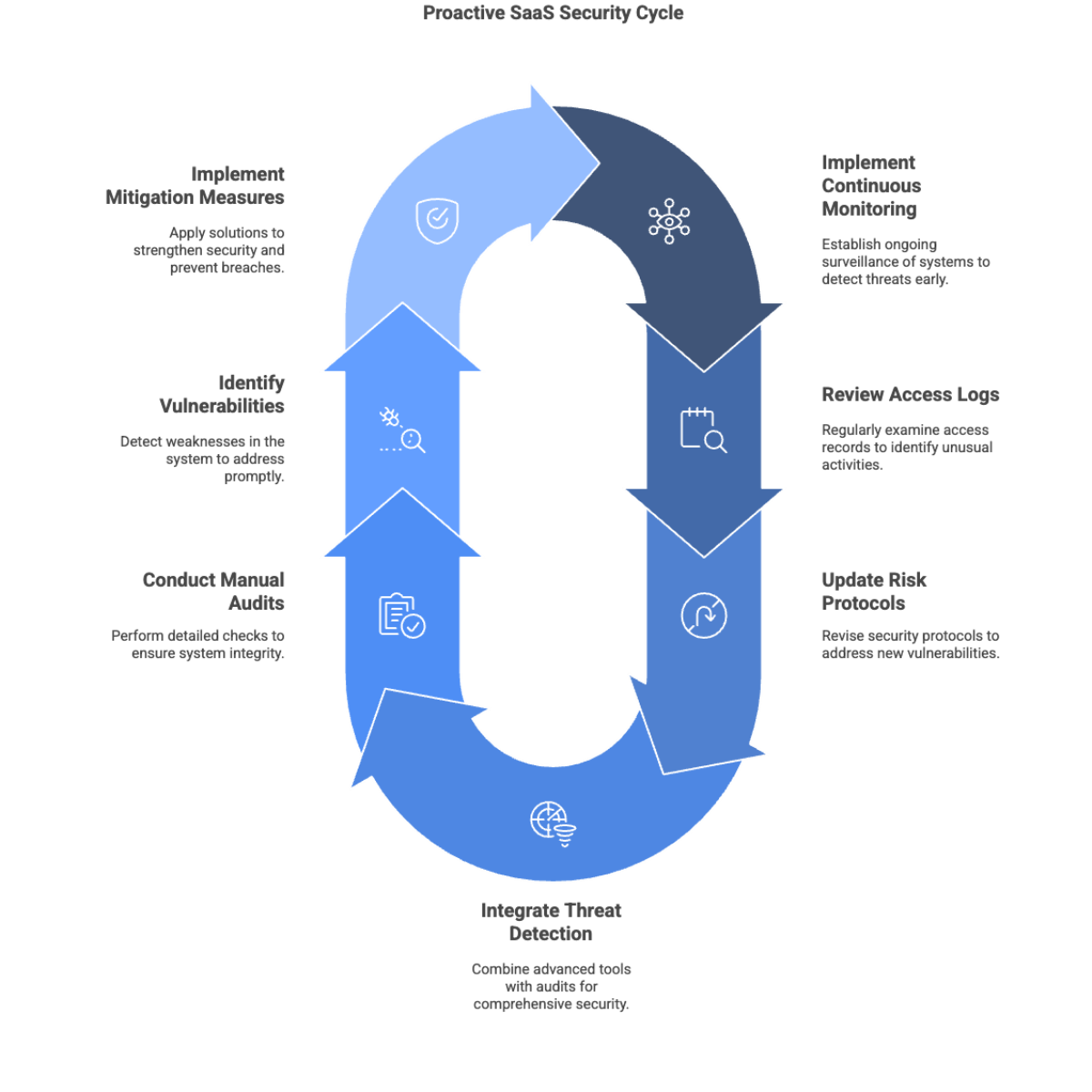
Recent research by Obsidian Security estimates that SaaS breaches surged by 300% year over year in 2024, with attackers infiltrating core systems in as little as 9 minutes. This alarming statistic underscores the importance of a proactive risk management strategy. Instead of waiting for a breach to occur, organizations should implement continuous monitoring solutions, regularly review access logs, and update risk assessment protocols to stay ahead of potential threats.
Adopting a proactive stance means integrating advanced threat detection tools with routine manual audits to swiftly identify vulnerabilities and implement mitigation measures. This approach not only helps in preventing costly breaches but also reinforces the trust of customers and regulatory bodies by demonstrating a commitment to security.

Below are some common questions regarding SaaS risk assessments and the associated security measures:

SaaS risk assessment provides a systematic approach to identifying and mitigating the potential dangers associated with the extensive use of SaaS applications. By conducting regular risk assessments, organizations can protect themselves from data breaches, legal liabilities, and operational disruptions. The process—ranging from evaluating the confidentiality, integrity, and availability of data to reviewing vendor SLAs and performing continuous monitoring—ensures that risks are managed proactively and effectively.
Adopting robust risk management practices not only safeguards sensitive information but also fosters a culture of security and transparency. In a rapidly evolving cyber threat landscape, continuous risk assessment is key to maintaining a secure SaaS environment and ensuring business resilience. Ultimately, by following best practices and leveraging advanced security tools, companies can mitigate potential risks and focus on driving growth without being hindered by unforeseen vulnerabilities.

If you’re ready to gain deeper insights into safeguarding your SaaS environment and uncover hidden vulnerabilities, download our eBook SaaS Security Unmasked today. Equip your team with the knowledge and tools to build a more secure, resilient SaaS infrastructure.