

Monday, April 21, 2025
Kim Jamerson
IT, legal, and compliance departments often take the lead on data privacy, but this business‑critical issue requires support from the entire company. That’s especially true if employees use software‑as‑a‑service (SaaS) applications, where customer and company data resides in the cloud, often in multi‑tenant, shared environments.
Effective data privacy policies enable organizations to build customer trust, manage risk, and remain legally compliant. This article explores SaaS data privacy regulations and fundamental steps every business should consider to protect themselves.

SaaS data privacy is the collective effort by SaaS providers and their customers—organizations and individuals—to ensure that data processed and stored in SaaS applications is protected. These protections encompass everything from data security and management protocols focused on breach prevention (e.g., hacking threats) to decisions about what information to collect and how it’s used and shared (e.g., internally and with third parties).

When you use SaaS platforms, you’re trusting those providers to handle your company data securely and responsibly. Every piece of information you upload—from prospective customers and sales pipelines to employee benefits and evaluations—is now stored in the cloud and potentially accessible by people who shouldn’t have access.

Given the vast quantities of sensitive data now housed in SaaS solutions, finding a provider compliant with relevant data privacy laws and industry standards is a baseline requirement when selecting a platform.
You should consult with your IT and legal teams to determine what regulations apply to your business, which can be impacted by your vertical and the types of data you’re capturing. However, here are a few key rules and standards associated with regulatory compliance.
GDPR is a European Union (EU) law that governs how companies collect, store, and process personal data. Even if your company isn’t based in the EU, you must comply if you have EU‑based users or customers or use a SaaS provider to house EU data.
Key GDPR components include:
Penalties for non‑compliance can be costly. Fines for serious violations can reach €20 million or 4% of annual global revenue, whichever is higher. For example, the Irish Data Protection Authority fined Meta €1.2 billion in 2023 for violating GDPR with its Facebook platform.
HIPAA is a US law establishing federal standards to prevent disclosure of sensitive patient health information (PHI) without patient consent. If your SaaS provider stores or processes PHI, it must comply with HIPAA, which includes administrative, technical, and physical safeguards to ensure confidentiality and prevent unauthorized access. Additionally, the law mandates timely notification to individuals and government agencies if a PHI breach occurs.
SaaS vendors serving healthcare organizations often need to sign a business associate agreement (BAA) committing to HIPAA compliance.
Penalties include civil fines ranging from $100 to $50,000 per instance and criminal charges, including fines and imprisonment, depending on the type and severity of the violation.
The EU isn’t the only regional data privacy law. Many other regulations might apply depending on where your business, employees, users, and customers are located, including:
In addition to regulations, there are several certifications that your business and your providers can get to demonstrate a commitment to best practices for data privacy and security. In fact, many privacy laws require one or more of these certifications.


SaaS vendors that take data privacy seriously implement technical safeguards and organizational policies focused on protecting user data. Here are a few things to look for when evaluating a provider.
Encryption transforms data into a format that is unreadable without an authorized decryption key. It’s a fundamental defense against unauthorized access. Look for vendors that address encryption both “at rest” and “in transit.” Advanced Encryption Standard AES‑256 is considered the gold standard for securing cloud environments.
Multi‑factor authentication enhances security by requiring multiple forms of verification, such as a username and password plus a code sent via text or through a mobile authentication app like Authy or Google Authenticator. Coupled with single sign‑on (SSO), these security measures keep unauthorized people or processes from accessing your applications and data.
Access controls dictate what users can see and do in an application. They come in three main flavors:
Regulatory requirements often come into play here depending on the type of SaaS application and what kinds of data will be stored in it. Highly sensitive information may require a "zero‑trust architecture" (ZTA), which assumes no user or device is inherently trusted and requires continuous verification and strict access controls for every request.
Audit logs track user activity and system changes. They can help you identify suspicious behavior and prove compliance in the event of a regulatory audit. Common capabilities include:

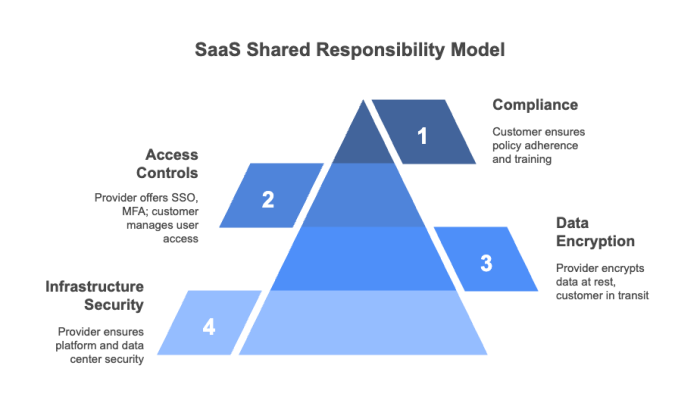
The shared responsibility model in SaaS outlines the data privacy and security responsibilities that both a SaaS provider and you, its customer, need to do to ensure compliance with organizational policies and governmental regulations.
A well‑designed framework will clarify who’s accountable for securing which aspects of the platform and the data housed within it, for example:
| SaaS Provider Primary Responsibilities | Your Primary Responsibilities |
|---|---|
|
Infrastructure and platform security
Security updates and patches Physical security and redundancies Data center security Data encryption at rest Robust features (e.g., SSO, MFA, access controls) |
Security configuration (e.g., SSO or MFA)
User access management (RBAC/ABAC) Compliance policies & employee training Data backup and recovery Data encryption in transit and key management |
When selecting a SaaS platform, look for providers that offer functionalities to aid with meeting legal and regulatory requirements, but remember, you’re ultimately responsible for ensuring employees comply with company policies and data privacy laws.

SaaS data privacy audits assess software providers’ compliance with data privacy regulations and best practices to ensure secure data handling and protect customer information. Before selecting a new vendor, you should conduct these evaluations and periodically re‑audit existing providers.

Consult with your legal, compliance, and IT teams to determine your precise privacy and security needs based on the type of SaaS solution, but here’s a high‑level view of what to examine.
| Area | Key Points |
|---|---|
| Certifications & Attestations | SOC 2, ISO 27001, NIST CSF, CSA‑STAR, HIPAA BAA |
| Compliance | Alignment with applicable data privacy regulations |
| Data Residency & Storage | Storage locations, residency options, encrypted geo‑redundant backups |
| Privacy Policy & DPA | Collection and use, retention periods, breach notifications, third‑party vendor oversight |
| Features & Functionality | MFA, SSO, user access controls, audit logs, monitoring |

Depending on the size and complexity of your SaaS footprint, you may find yourself asking, “Are there tools that capture, validate, and monitor SaaS data privacy and security data?”
The answer is yes. Numerous solutions on the market are designed to help you get real‑time visibility into the privacy and security posture of your company and your SaaS vendors. They can give you confidence that you’re in compliance and the ability to prove it to customers, regulators, etc.
A few examples include:

Ensuring SaaS data privacy and security can feel daunting, given the ever‑changing regulations and emerging security threats. That’s especially true when you consider that the average organization uses a whopping 112 SaaS applications.
As a business leader, you’re not expected to master every technical detail, but you should have a baseline knowledge to ask the right questions to ensure vendors are evaluated carefully and that your organization complies with privacy standards and regulatory requirements.
Want to learn more? Check out SaaS Security Unmasked and Data Privacy in the SaaS Era.
